Proxy LTE, 5G, Mobile proxies
You might hear about 3G, 4G LTE, and 5G proxies and notice that they are more costly than Residential. Let's find out the difference between them and other proxy types and how to get maximum value from mobile proxies.
If you want to recap what popular proxy types are available on the market and what client cases they suit best - please read the Pyramid of efficient scraping article.
Providers promise the highest success rate and absence of Captchas. Is this true?
In general, yes it is, but there are nuances that we will discuss with you now.
The unique feature of such proxies is that there is no value in banning the client IP addresses on the target resource side. The core principle of how mobile networks are connected to the public internet contains an abstraction layer - the real and unique addresses of mobile devices differ from the IPs they get when reaching the public internet. They are not visible outside of mobile ISP networks. When the mobile device reconnects to the network its public internet IP address changes naturally. So, if the provider bans the user's IP address with suspicious behavior, the next minute, this address will belong to another person, and such measures will affect the product and financial metrics of the target service in a bad way - the conversion rate will fall.
Why is this feature unique compared to the other proxy types?
- Banning the DC IPs is the easiest task for the target resource. They will determine that your IP belongs to the DC connection type using one of the popular IP DBs: MaxMind, IP2loc, IPQualityScore, etc. There are existing integrations for such DBs into customer-facing services like Nginx. So the target service can ban you starting with the first requests, not the single IP address but the whole /24 network - meaning 254 IPs(usually you rent blocks of IPs).So you will pretty quickly run out of rented IPs
- It is harder to ban Residential IPs because there is no reason to ban you starting from the first request if they are not exhausted and spammed(You can see popular providers IP quality (You can see popular providers IP quality here). But, if the user demonstrates suspicious behavior(untypically high request rate, fake or inconsistent fingerprints, etc) the IP address will be banned. The only thing the user can do - is rotate the IP address and continue with another one. But there are no infinite IPs in any proxy provider, and when they run out - you have to use another provider. Integrate, managing and switching proxy providers will require additional work, and you can't ask the proxy provider to give you more unbanned IPs now ).
- If you are using a dedicated mobile proxy farm, you can rotate IPs as frequently as you want, and with a high probability that new IPs won't be banned. Also, some providers let you change the TCP fingerprint of your outgoing sessions, Rotating Resi can't do that for you.
Two different products but one name
Real residential devices with cellular connection
You might find mobile proxy products in big and well-known proxy providers' offerings like: BrightData, Smartproxy, IProyal, Infatica NetNut SOAX Oxylabs, Bright, Oxy, Smart, etc But there are nuances of what they are made of. Some vendors are conducting traffic using real users' devices like Residental proxies, but traffic goes via cellular networks: 3g, 4g LTE, and 5G.
Such a solution has a pross:
- The amount of devices / IPs is big.
- GEO location is more diverse and has better coverage.
- Some features, like sticky sessions and session length from the Rotating Resi product, might also work.
and conns:
- Connection quality is pure: latency and losses are worse than Resi and Dedicated Mobile Farms.
- Session length is less predictable, and you can't control it. Actual resi device can disconnect at any second.
- You can't rotate the exact device IP address when you want.
- You can't change the TCP fingerprint that the target service might collect.
Dedicated mobile proxy
The alternative solution is dedicated mobile proxy farms; they also might have the name of private 5g farms. This is an industrial solution created specifically to provide proxy services. Usually, it looks this way: a bunch of high-speed LTE/5G modems connected to the Linux box in someone's apartment with high-quality cooling back connected to the public internet service. It is placed in an exact physical location. It provides some sort of HTTP API to let you restart(disconnect/connect) the modems to rotate IPs. This is how it might looks:
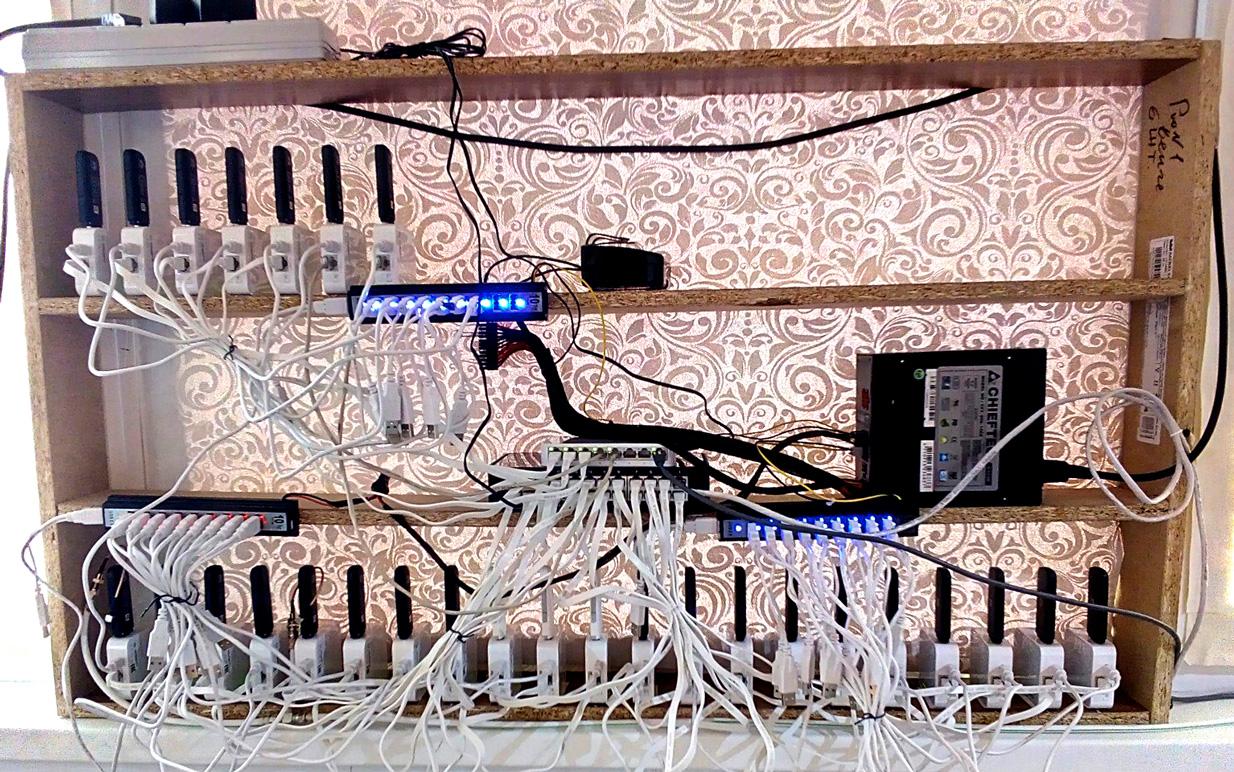
has a pross:
- Rotations are limited only by mobile ISP
- Pretty often, you are using them as dedicated
- New IPs will be clean
- High and stable connection speed - up to 450-500Mbit/s
- Session length up to 24h
and conns:
- Pure GEO location coverage. ISP will output traffic centrally near the place of presence.
- More expensive
- Usually, you find such service in Telegram or Discord and support, contract legal aspect will be far from top well know providers
I have to say that ISPs in general are not happy with such customers and have been limiting them for the last few years.
- Removing flat prices for the traffic - unlimited tariffs.
- Limiting frequency of IP address change
High level diagram of Dedicated mobile proxy solution
I'll simplify the internal structure of the Mobiles ISP solution and will try to explain the big picture.
- BTS - Base transceiver station
- RAN - Radio Access Network
- CN - Core network
- GGSN - gateway gprs support node.
Let's split the whole mobile ISP solution into three pieces:
- RAN is responsible for communicating user devices with the core networks.
- Core networks conduct and route to the "write place" users' traffic. Both these two use internal mobile-specific protocols and addresses. They can't speak the same language as the public internet, which is based on TCP/IP.
- The GGSN might be considered the router that lets different networks with different protocols and addresses speak. The amount of IPs on the public internet that belong to the mobile ISP is limited, and provider will try to do their best to make the solution cost-effective to avoid unnecessary steps of conducting traffic to distant GGSN(router). That's why there are no transparent IP addresses for mobile ISP clients.
Let's construct the solution step-by-step
- No proxy provider at this point only legitimate users, ISP providers, and target resources. Yes, even at this stage target resources can't distinguish one user from another stably and predictably. It sees a pool of IPs that belong to the GGSN gateways. Exact IPs from this pool are temporarily used by the exact users with mobile devices. Then they change, the same user will have another IP and the previous IP will belong to another user.



