Guide for ProxyChick - Open source proxy testing tool
I'll guide you on how to measure proxy service speed and performance and how to test that it works for your specific case like UDP.
Get started
The binary
How to get the tool - you can download the binary for your arch on the Github release page or build it from source(Golang 1.22 needed).
For MacOS you need to first time launch it with right-click and open the menu item cause it is not signed with Apple Dev cert. After that, you can launch it as any other command line tool.
Call it using the -version param to verify that it works fine.
./proxychick -version
proxychick 0.3.0, commit a8b3067f77ab2ed4dd5a147fe762766ae9b699d2, built at 2024-03-23T12:09:50Z
Proxy list
To evaluate proxy service we need access to it, so please copy URL or proxylist file form the vendors dashboard. ProxyChick supports next proxy protocol and trasnport protocol combinations:
1.TCP from client to proxy server and TCP inside the tunnel(from client to taget):
- http
- https
- socks4
- socks4a
- socks5
- socks5h
2.TCP from client to server and associate UDP (from client to server and than to target):
- socks5
I suggest to start with most popular HTTP TUNNEL proxy protocol, this means that you URL should start with http://. A few examples:
http://package-6166123-country-ie:deadbeef@proxy.soax.com:5000
http://deadbeef:wifi;;;;@proxy.soax.com:9000
Let's launch our fist test
Let's assume your proxy list file is next /path/to/proxylist.
Then you can launch the test this way
./proxychick -i /path/to/proxylist -loop 100
-i <file path>- read proxylist file from defined path.-loop <int>- repeat proxylist file content N times.
Your terminal window will looks this way. If you want to save the result table in a CSV file instead of having them in your STDOUT, add -o cmd param.
$ ./proxychick -i /path/to/proxylist -loop 100
100% |███████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| (100/100, 10 it/s)
proxy,result,targetStatusCode,proxyStatusCode,latency.ttfb,latency.dnsResolve,latency.conn,latency.tlsHandShake,latency.proxyResp,ProxyServIPAddr,ProxyNodeIPAddr,error
http://package-6166123-country-ie:deadbeef@proxy.soax.com:5000,true,200,200,5554,3,41,5253,146,23.109.113.236,109.77.24.212,
...(All other rows with stats here)
http://package-6166123-country-ie:deadbeef@proxy.soax.com:5000,false,0,200,0,4,40,10004,145,23.109.113.236,,net/http: TLS handshake timeout
Success Rate
+-------+-------+---------+
| VALUE | COUNT | PERCENT |
+-------+-------+---------+
| ok | 99 | 99.00 |
| error | 1 | 1.00 |
+-------+-------+---------+
Errors
+---------------------------------+-------+---------+
| VALUE | COUNT | PERCENT |
+---------------------------------+-------+---------+
| ok | 99 | 99.00 |
| net/http: TLS handshake timeout | 1 | 1.00 |
+---------------------------------+-------+---------+
Taget HTTP status codes
+-------+-------+---------+
| VALUE | COUNT | PERCENT |
+-------+-------+---------+
| 200 | 99 | 99.00 |
| 0 | 1 | 1.00 |
+-------+-------+---------+
Proxy HTTP status codes
+-------+-------+---------+
| VALUE | COUNT | PERCENT |
+-------+-------+---------+
| 200 | 100 | 100.00 |
+-------+-------+---------+
Latency
+--------------+------+------+------+------+------+------+------+
| NAME | 50 | 75 | 85 | 90 | 95 | 99 | 100 |
+--------------+------+------+------+------+------+------+------+
| TTFB | 1016 | 3164 | 4691 | 5553 | 5714 | 7997 | 8236 |
| DNS resolve | 4 | 4 | 5 | 5 | 5 | 5 | 5 |
| Connect | 41 | 42 | 42 | 43 | 43 | 43 | 43 |
| TLSHandshake | 316 | 510 | 2230 | 5235 | 5306 | 5745 | 5759 |
| ProxyResp | 155 | 2465 | 2467 | 2826 | 3368 | 3400 | 3402 |
+--------------+------+------+------+------+------+------+------+
Interpret the results
-
Success Rate - counts the amount of successful HTTP replies from the target resource. If a client isn't able to get a reply in a defined time(
-tocmd param) it will count as an error. -
Errors - break down of erros ocured during the test. As you can see in this case 1 of 100 requests failed because of the TLS session timeout. We succesfully got reply from proxy server with acceptable latency but than TLS session negotiation btw client and traget resource takes too long.
-
Target HTTP status codes - aggregated target host replies. 0 - means error ocured on lower layers(Transport, Network, etc). You can define target http URL with cmd param
-t. By default, it uses https://api.datascrape.tech/latest/ip. It's handy to use services that provide proxy node ip_addr in reply. -
Proxy HTTP status codes - if you credentials are correct and you haven't exceeded traffic limit it should be 200 OK in the vast majority of cases.
-
Latency - here you can find the total latency breakdown with distribution. For HTTP protocol we measure next events:
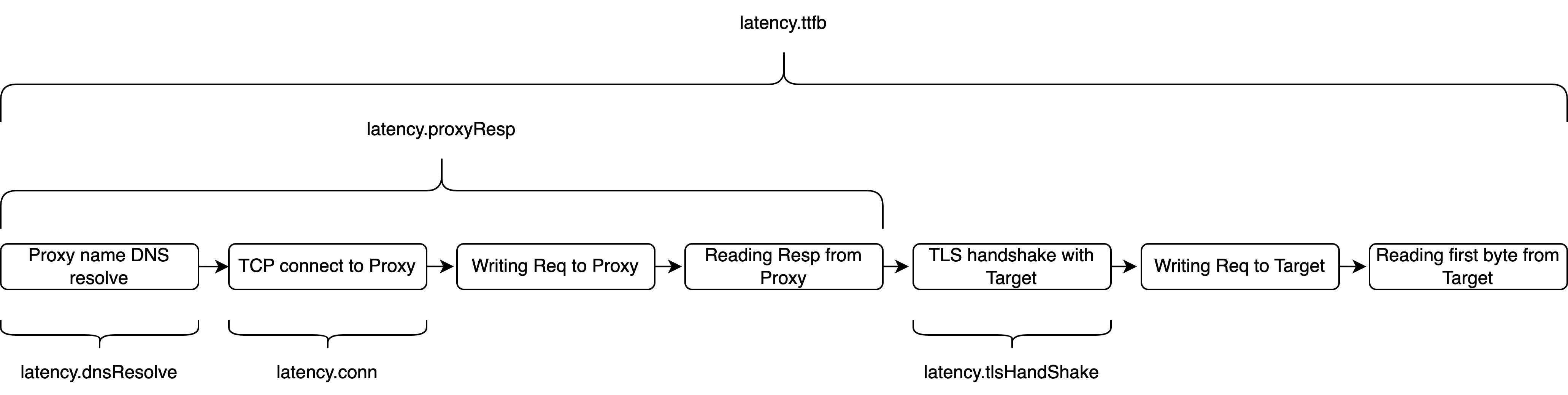 picture here
picture here
Latency table header contains the next numbers 50, 75, 85, 90, 95, 99, 100 they are precentiles. Values in rows are quantiles. You can read them the next way - "TTFB for 50% of calls in our test feats into 1016 ms(milliseconds)". This means that, if distribution remains the same with a 50% chance your next call will fit into this value. With 75% probability feats into 3164ms, etc
Proxy protocols
For HTTP calls standard Golang library is used and all mentioned protocols are supported. From practical perspective if you client support socks5 - it's good choose from perfronce perspecive. If you want to proxy UDP traffic - you have to use socks5. If you have oldfashioned client that supports only HTTP - this is your choise.
You can provide proxy URLs in any of the following formats:
1.Complete URL with protocol scheme
socks5://deadbeef:wifi;;;;@proxy.soax.com:9085
The URL will be used as it is and provided scheme will be used to connect to the proxy server.
2.loign:password@host:port
deadbeef:wifi;;;;@proxy.soax.com:9089
Only the protocol scheme will be added. The default one is http you can define another with -p cmd param.
3.host:port:login:password
proxy.soax.com:9089:deadbeef:wifi;;;;
This format is popular among narrow-scope apps like sneaker purchase bots. This proxy string will be converted automatically, protocol scheme will be added the same way as for #2.
UDP over socks5
Socks5 support was implemented with the help of the ghost library. The only disadvantage - it's resolving target resource on the client side. I've created simple echo server to test UDP. Using it, you can see your public ip_addr via UDP the next way. Send any data and wait till connection will be closed. Server will respond you back with your ip_addr, timestamp and your original string.
$ echo -n "34651CB8-23A1-4E19-8272-39D2CE16ABA8" | nc -4u -w1 api.datascrape.tech 80
{"clent_ip_addr":"78.18.38.199","client_msg":"34651CB8-23A1-4E19-8272-39D2CE16ABA8","epoch":"1710513296"}
Let's call the same server via ProxyChick
$ ./proxychick -i /path/to/socks5-proxylist -transport udp
100% |██████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| (1/1, 2 it/s)
proxy,result,targetStatusCode,proxyStatusCode,latency.ttfb,latency.dnsResolve,latency.conn,latency.tlsHandShake,latency.proxyResp,ProxyServIPAddr,ProxyNodeIPAddr,error
socks5://deadbeef:wifi;;;;@proxy.soax.com:9000,true,0,0,455,0,0,0,50,23.109.113.228,2.34.207.241,
Success Rate
+-------+-------+---------+
| VALUE | COUNT | PERCENT |
+-------+-------+---------+
| ok | 1 | 100.00 |
+-------+-------+---------+
Errors
+-------+-------+---------+
| VALUE | COUNT | PERCENT |
+-------+-------+---------+
| ok | 1 | 100.00 |
+-------+-------+---------+
Latency
+-----------+-----+-----+-----+-----+-----+-----+-----+
| NAME | 50 | 75 | 85 | 90 | 95 | 99 | 100 |
+-----------+-----+-----+-----+-----+-----+-----+-----+
| TTFB | 455 | 455 | 455 | 455 | 455 | 455 | 455 |
| ProxyResp | 50 | 50 | 50 | 50 | 50 | 50 | 50 |
+-----------+-----+-----+-----+-----+-----+-----+-----+
As you can see test completed sucessfully cause result column has value true, server saw the connection from ProxyNodeIPAddr == 2.34.207.241 and it differs from our original ip_addr from the direct call with Netcat.